In this material, Rucriminal.info will reveal who is behind Match systems (aka Plain chai).
So, Match systems, aka Plain chain, position themselves as blockchain investigators, that is, people who help search for wallets and transactional connections between them in various blockchains using various software. The main service that brings them money is the return of stolen money for %. The reward amount varies from 5 to 50% and depends on the amount of theft, the complexity of the case and the resources involved. Often, Match systems representatives take an advance of around 10% of the amount. By the way, they never return the advance, citing “we did what we could, here is a certificate of the flow of funds.” And this, by the way, is Scam number 1. Blockchain analysts from Match systems have such cases every third, and the advance amounts vary from $1,500 to $5,000. Usually, victims easily part with such amounts in exchange for the hope of getting at least something back. But this is just the beginning...
According to a source from Rucriminal.info, having received a request for an investigation and a refund, Match systems employees create a chat in Telegram, assigning a serial number to it (now there are already more than 600 of them, which means more than 600 potential scams for Scam 1 or Scam 2 later). In the chat you are asked to fill out the following form:
1. Telegram of the contact person (link to profile)
2. Approximate amount of damage (in dollars)
3. Incident start date
4. Incident end date
5. Address(es) of the wallet(s) from which the theft occurred
6. Hashes of transactions through which the theft occurred (if any)
7. Attacker’s wallet addresses (if any)
8. Description of the situation (as detailed as possible)
9. Information about the attacker (if available)
10. Place (city, country) where the theft occurred
11. Place (city, country) where the injured person permanently/temporarily lives (or lived at the time of the incident)
12. What is the desired result (prosecution under criminal law, return of funds, etc.)
13. Additional materials on the case (correspondence, screenshots, documents, etc.)
Then the fun begins. The most ordinary blockchain analysts with a salary of $1500-2000 +% of the refund amount, having in their arsenal the answers to the questions from the questionnaire above, sit down and trace the path of the stolen crypt with their hands. Along the route there may be mixers, bridges, swaps, whatever, but something else is important to you and me - where the attacker wants to “locate”. So, if funds end up on any exchange, and most often this is what happens, they can be seized there and then written off in favor of the victim. Moreover, often, stolen assets can end up on the exchange not from the original attackers, but generally from innocent third parties. But this will no longer matter in the scheme. What happens next? Pure magic from the masters of forgery.
Attention, the tough stuff is about to begin. So, having “extensive experience in law enforcement work” (more on this separately), Match systems employees send an order to seize digital assets (sometimes cryptocurrencies or digital currencies) as part of an inspection or as part of an initiated criminal case, or even a court decision .

An example of a court decision on the seizure of cryptocurrencies
“So what?”, you ask, “this is a document and everything is legal.” Indeed, this document is grounds to at least freeze the account and investigate further. If, for example, the account is associated with an attacker, then it is stupid to argue here and the injured client will receive his money, or at least part of it. Well, if it’s not connected, then you can’t argue against the document and the exchange believes the documents, not the users. As practice shows, Match systems don’t care and they (extort) demand their client’s money in order to get the % faster. It is extremely difficult to obtain such a judicial or law enforcement document in a real court case. Based on experience it will take at least 3 months. and this despite the fact that Russian courts and law enforcement officers do not treat this topic very well.
And so, someone from Match systems brings such pieces of paper in just 1-2 WEEKS, after they understand that the money is on one or another exchange. We are gradually approaching Scam number 2 - FORGERY or simply FAKE. This is where the great variability of such forgeries comes into play, because behind the documents there are always real people in any structure and this cannot be done without accomplices. This is what law enforcement officers, now the founders of Match systems, did together with the existing ones. Sometimes, when the situation does not require real signatures and names, Match systems simply falsifies court documents. By the way, many such documents end up on the Garantex, Huobi and Binance exchanges, etc.
By the way, one of these werewolves, whose name was regularly signed on Match systems documents, was detained. Investigator Antonina Shakina from Moscow is accused of falsifying a court decision to seize an account on the Garantex crypto exchange. She shared the money from him - several million rubles - with Match systems. Basics The authors and authors of the scheme are now carefully trying to hide their participation in the case, hiding behind employees of the Garantex exchange and the detained investigator, whom they skillfully framed, knowing about her pregnancy.

Alleged Match Systems accomplice, investigator Antonina Shakina.
According to the source of Rucriminal.info, what the founders and employees of Match systems are doing is a serious criminal offense that harms innocent people for the sake of the commercial interests of former and current werewolves in uniform.
The Match systems website also has many services related to their developments, which they are actively trying to promote in the former USSR, but without much success. Let's take a look at what these services are. First of all, to get a demo of a transaction monitoring product, you need to wait longer than they create fake documents for exchanges, but that’s not the point here. The product cannot be used for real work; it contains outdated databases of the Ministry of Internal Affairs and the FSB of the Russian Federation, and the analysts themselves use paid versions of software from Crystal and Chainalysis for investigations.
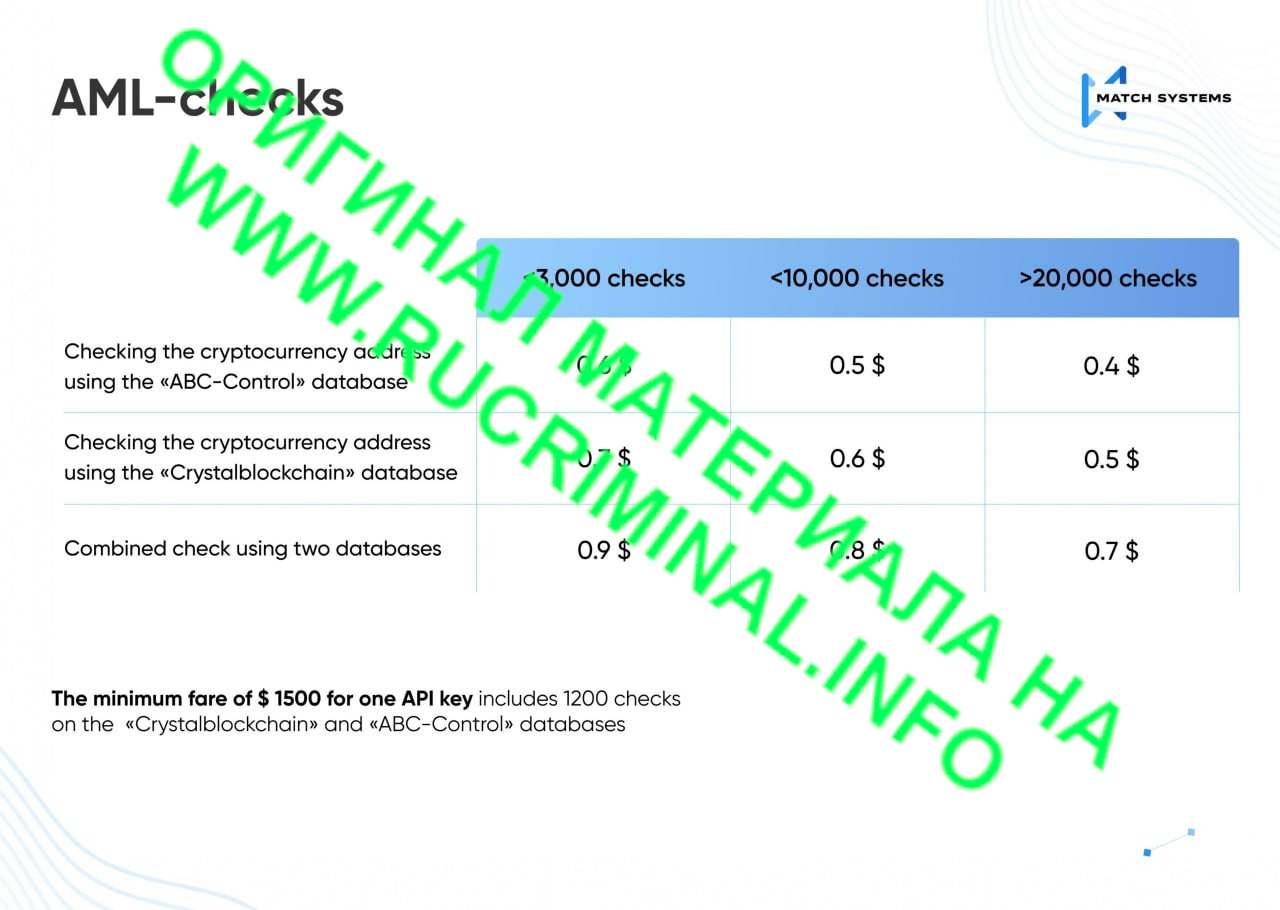
ABC-Control database is nothing more than illegally obtained databases of the Ministry of Internal Affairs, Investigative Committee and FSB of the Russian Federation, as well as purchased databases of dirty addresses from the Darknet. Crystal is data that Match Systems pays for themselves and does not have the right to resell this data in this format.
Match systems make money exclusively from pseudo-detective and investigative activities. It seems that Match systems understand that the topic of document forgery will not last forever and you can try to play at a startup. Scam number 3 - “look investors, we have revenue (received from Scam 1 and Scam 2) and our own software (in reality not working and disguised as someone else’s solutions, as well as unauthorized databases of the Ministry of Internal Affairs, Investigative Committee, FSB of the Russian Federation), please give us money". By the way, it was for Scam number 3 that a separate company, Match systems, was created in Singapore with an office in Dubai, while all employees actually continue to be in Moscow and work in the Plain chain, which they originally were, trying to sell their services to Russian banks and government agencies. The general director of an LLC in the Russian Federation is nominal, here is an extract. In addition, there is a company in Kazakhstan, where the general director is already one of the founders, Kutyin.
Having a difficult background, incompatible with venture investments, Match systems fictitiously split up to hide the connection of the founders with law enforcement agencies of the Russian Federation. If funds suddenly read this, then Scam 1+Scam 2+Scam 3 = bold “RED FLAG”.
And finally, who are they, werewolves in uniform, who decided to get rich from the imperfections of cryptocurrency compliance systems, oversight (or collusion) of exchanges and attract investor money for this by telling tales about a successful software startup “from Singapore”.
Founders
1 Dorzhinov Ice Nikolaevich

ex-analyst at the Center for Internet Security of the FSB of the Russian Federation
lives in Dubai, UAE
co-founder of Match systems, responsible for analytics and investigations, “borrowed” databases of tagged addresses after leaving the FSB
2 Kutin (also Kutin) Andrey Olegovich

lives in Dubai, UAE
ex-operator of the Main Directorate for Drug Control of the Ministry of Internal Affairs of the Russian Federation
CEO Match systems
actively travels and attends crypto and security events on behalf of the company, is married to the daughter of a former high-ranking official involved in the oil business.
3. Georgy Rakhaev

advocate
Moscow City, Federation Tower, office 4207
co-founder and investor in Match systems, actually provides “legalization” and contacts with werewolves in uniform
current lawyer at the Moscow Region Bar Association 50/9246 (this investigation was sent to the bar for a petition to revoke the license)
creator of a fraudulent law firm collecting orders for Match systems
4. Roman
Director of Development and Sales
Moscow and Dubai
Most of the employees and founders are directly related to law enforcement agencies of the Russian Federation. This is where all the diagrams and data come from. Databases of “dirty” addresses are “merged” legally.
Joseph Trostinsky
To be continued
Source: www.rucriminal.info






